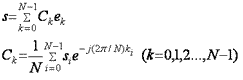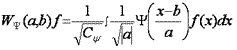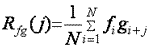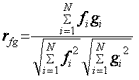Analysis and design of computer information processing methods
applied to bank-note sorting machines and validators
Dissertation abstract
Preface
The currency authenticity verification is one of
the most labor-intensive banking operations. It's implemented not only by
experts in this field but also by regular cassiers. Therefore a well
technically equiped working place is one of the chief requirements for the
successful realization of counterfeit detection functions.
The number of detected counterfeit bank notes
and what is more important their quality continues to rise despite the constant
anti-counterfeit measures undertaken by all the countries around
the world. According to Currency News - the International Currency
Association herald
[1], the number of detected euro counterfeits has grown from 167118 in
2002 to 594223 in 2004. Together with the number of counterfeits grows the
need to improve the equipment as well as the methods of currency
authenticity verification.
The main tendencies in the development of
currency validation equipment include joining up several (magnetic, infra-red,
etc.) sensors at the same validation device, elaboration of unit validation
device architecture and it's connection to computer.
As a consequence of such tendencies there is a
need of special software to enable the processing of sensors'
information and optimal algorithms that will not only speed up the
information analysis, but also allow for new bank note
series issuing.
1. Research field overview
1.1 Bank note protection methods
The authenticity verification methods
are closely associated with current counterfeit protection technologies,
used in bank note, securities, identification and plastic
cards manufacturing. As regards currency protection today's protection
techniques include [2],[3]:
Technology - contains the techniques based on the calculation of certain
object properties , such as
-
paper composition
-
the preset composition and characteristics of colour substances
-
special paper surface treatment
-
water mark
-
inclusion of colour and luminescent fibers in paper mass composition
-
preset composition of protective inclusions
-
protective thread (synthetic or metallic)
-
relief printing
-
Kipp-effect - special kind of printing detectable under specific
lighting only
Graphic level - a set of methods based on use of special forms,
size characteristics, means of location and combination of graphic image
elements:
-
pseudo water mark
-
giilloshire frames
-
microtext
-
protective grid (e.g. antiscan grid)
-
diverse form and combination of fonts
-
special micro-deffects of graphic elements
-
asymmetric graphic image location
-
image superposition – front and reverse side printing insuring their exact
matching or supplement.
Physical level - a set of methods based on physical properties of objects
and substances:
-
hologram and methogram label elements
-
luminescent substances combination
-
use of substances that turn luminous in IR or UV rays
-
use of OVI paints changing color depending on the angle of vision
-
use of protective magnetic code thread - metallic thread including magnetic
elements, the combination of which encodes bank note denomination
1.2 Protection degrees
The combination of diverse bank
note protection methods insures the reliability of protection and makes
for the following classification of currency protection degrees[1]:
-
Simple or visible: water marks, relief printing
-
Complicated, needing special equipment to detect it: magnetic, UV and IR
protection
-
Special protection - the combination of protective features known by currency
developers and manufacturers only, which is a State secret
1.3 Technical means of authentification
The great number of protection techniques and a
set of requirements as for the depth of authentification make for a wide range
of currency counting and validation equipment that can be classified by 3
groups
[1]:
-
not automated (simple manual visualisation devices)
-
automated (semi-automatic bank note detectors, equiped with sensors)
-
expert complexes (currency sorters able to detect the elements of special
protection)
1.4 Leading researchers and manufacturers
Today the leding manufacturers of the bank
note counting, sorting and validation devices include such producers as
DeLaRuе (England)[4],
SPEED (Japan)[5],
PRO (Japan)[6],
SCAN COIN (Swiss)[7] . The devices of the first and third group of
technical means classification are also produced by such home producers as
«Vildis» (Moscow), «Regula» (Minsk), «Systema» (Moscow),«Spectr»(Nikolaev)[8].
2. Existing methods analysis
The analysis of the great range of counting,
sorting and validation devices makes it possible to classify basic
authentification methods:
-
geometric size control - insured by optic sensors that detect the beginning and
the end of the bank note passing through the transportation mechanism. The
length and the width of each bank note is computed with use of data saved by
encoder connected to transportation shaft of the mechanism.
-
IR label presence and location control. Control asserted by IR sensors. The
value of light reflected from the bank note surface is estimated by the sensors
and determines the presence of IR labels
-
paper quality control with use of UV light source and photoreceivers in visible
spectrum part. The controlled bank note passes under the UV rays (wave length=
365 nm or 246 nm). Special paper used for bank note manufacturing is not
luminous in visible spectrum part. The only luminous parts of the bank
note are those that include special protective elements luminous in the visible
part of light spectrum.
-
paper quality check with use of tri-colour optic sensors
-
magnetic thread and elements presence and location control with use of magnetic
heads. Magnetic heads' sensitive areas detect magnetic marks included in
protective magnetic thread. The magnetic heads digital response
processing with standard comparison makes for a
conclusion authenticity conclusion.
3. Research highlights
3.1 Problem actuality
The conducted analysis has shown a poor offer of
money counting devices with automatic magnetic code protection control.
Although this kind of protection is one of the most trustworthy (there wasn't a
single case of magnetic code falsification within 20 years of it's use in
English pound currency), it's verification is conducted mostly by the
devices of expert class only.
Besides, in 2004 the magnetic
code currency protection has found it's use in Ukrainian hryvnas.
Therefore the problem of development and introduction of automated devices
implementing magnetic code verification, that can be used at the cassier
level can be refered to as the problem of today.
3.2 Practical value of research
The development of information processing
methods aimed at magnetic code verification will make it possible:
- to rise the equipment level of cassier working place;
- to improve the trustworthiness of currency authenticity
check results as bank note falcification with exact immitation of magnetic
code protection requires a high level of technology and is unlikely.
3.3 Research steps
3.3.1. Code standards identification
Open sources do not contain any information about
magnetic protection code sequences. That makes it necessary to identify
standard code sequences using magnetic fields visualisation means
[9],[10].
It is proposed to take 5,10,20,100,200,500 euro bank notes as reasearch
samples. Figure 3.1 represents the results of standard identification
step.
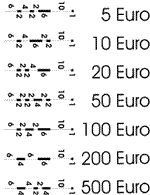
Fig.3.1
- Standard euro codes
Magnetized parts are indicated with use of bold black lines.
The length of magnetic code spaces is in mm .
3.3.2. Magnetic code reading and computer information input
Magnetic code is read by means of successive
registration of remanent magnetism of protective magnetic thread parts in
the parts which represent implanted ferromagnetic material particles. To
register magnetized parts of the thread magnetoresistive heads
[11],[12],[13] are
used in combination with amplifier and analog digital converter . Figure
3.2 represents the instance of signal of 20 hrvn magnetic code.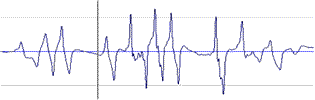
Fig. 3.2 - Digital magnetic code sequence of 20
hrvn. bank note
3.3.3 Data processing
The last, but not the least step of this
reasearch consists in magnetic code sygnal processing. Here the problem turns
into discrete nonstationary sygnal processing. Data analysis includes the
following steps described further.
3.3.3.1 Spectral analysis
To distinguish the information part of magnetic
code signal from it's noise part it is proposed to use sygnal spectral anlysis.
The information about noise frequency band will be useful at the next
filtration step of magnetic code sygnal processing. The following methods
allow to conduct the preliminary spectral analysis of a sygnal:
-
Discrete Fourier transform (DFT)[14 p. 34]
For a discrete sygnal represented by a sequence of N values DFT computation
looks like:
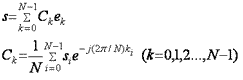
, where s - discrete sygnal, С - Fourier transform coefficients
-
Fast Fourier transform (FFT). This method represents a fast way of Discrete
Fourier transform computation. The use of this method speeds up the
process of Fourier transform calculations.
3.3.3.2 Filtering
To clear magnetic code sygnal from noise
there is a need of optimal filter calculation. Filter characteristics mostly
depend on the results of sygnal spectral analysis. It is proposed to use the
following methods to solve a problem of sygnal filtering:
-
Digital filter design. The output sequence of any filter represents the
initial sygnal and filter impulse response convolution. The task of filter
calculation consists of filter type (linear - nonlinear; recursive -
nonrecursive) and filter impulse response selection.
-
Wavelet filtering. Wavelets represent a useful mechanism of sygnal filtering
and preliminary processing of sygnal data[15],[16].
The essence of sygnal wavelet transform is in multiscale analysis which means a
sygnal decomposition with use of basis of functions exposed to multiple
dilations and shifts which assures sygnal representation both in time and
frequency space. The base functions are called wavelets if they are defined
in L2space, oscillate at absciss axis and meet zero value with
argument increment. The sygnal and wavelet convolution allows to
distinguish sygnal singularities at the point of wavelet
localization. Wavelet transform as well as Fourier transform represents a
sygnal decomposition in a basis of determined functions
[15].
Straight continuous wavelet transform is calculated using the following
formula: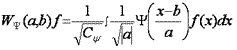
,where a and b are scale and shift factors of ψ function or
wavelet, Cψ – rate setting factor. Wavelet filtration algorithm includes the
following steps:
-
Wavelet sygnal decomposition
-
Threshold selection for each level of wavelet decomposition
-
Threshold filtering of detalization coefficients
-
Sygnal reconstruction
3.3.3.3 Feature detection
The features of magnetic code sygnals we are
interested in, that represent the beginning and the end of magnetized parts of
protective thread, include positive and negative piques. The exact localization
of particularities mentioned above has a great value for subsequent data
analysis. It is proposed to use the following methods to solve the problem of
feature detection in magnetic code sygnals:
-
Feature detection using wavelet analysis. The main particularity and the main
advantage of wavelet sygnal analysis is 2 domain (time and
frequency) sygnal representation. The time-frequency representation of the
sygnal in question makes for it's singularities localization
[18],[19],[20].
The features in question may include piques, bursts and threshold points. The
type of singularity we are interested in dictates the type of wavelet we are to
chose for analysis. One of the classical instances of wavelet feature
localization is a problem of R-piques detection in ECG processing
[21]. The coefficient amplitude is a main sign of local pique
in use of wavelet feature detection. Therefore the local coefficients' extremum
is the main indication of a local singularity.
-
Design of one's own feature localization algorithm. Defining exact indications
of sygnal piques (such as their length in time, their amplitude and their
number for a code length) makes for a creation of one's own simple feature
localization algorithm.
3.3.3.4 Classification
The fact that the magnetic code in question
coinsides with one of the standards defined earlier serves an authenticity
proof of the bank note in question. In case where the percentage of coinsidence
is low (e.g. lower than 80%), a hypothesis of bank note authenticity should be
denied, the bank note is either a counterfeit or defected. Therefore at the
final stage of researchthe problem of magnetic code classification is to be
solved.
-
Correlation analysis.
A cross-cprrelation function is one of a special characteristics of two
sygnals. This function is an indicator of both the differences in the form of
sygnals and their relative location on the time axis. For discrete sygnals fi
and gi (i= 0,1...N), their cross-correlation function is
calculated as:
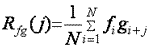
To evaluate the similarity of two discrete
sequences the correlation coefficient should be calculated:
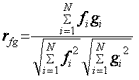
The coefficient value always belongs to the
range [-1;1]. If the value of correlation coefficient is close to 1, the forms
of two evaluated sygnals are similar. The use
of cross-correlation analysis is proposed to evaluate the similarity of
the magnetic code sygnal in question to each standard in the set of
standards defined at the earlier step.
4. Assumed scientific novelty
The analysis conducted on the state of equipment
for bank note counting and validation shows that presently there is a low
number of cassier level devices designed to read and process bank note
protective magnetic codes.
The objective of present master's project is the
development of an effective mechanism of magnetic code reading
results represented by digital sygnals.
The creation of effective information
processing algorithm in course of bank note validation by means of magnetic
code verification is viewed as a result of present research. It
must reveal new domains of Fourier and wavelet transforms as well as of
digital filter design and computation.
5. Conclusion
So far as a result of information sources
analysis we have a definition of currency protection techniques, their
classification and the evaluation of a protection degree assured by
each of these techniques. There are also the results of analysis conducted
on the developments made by leading manufacturers in the field of currency
counting and validation equipment. On the basis of this information it is
proposed to make a protection by means of partially magntized thread an
object of master's project research.
The analysis mentioned above has shown a poor
offer of money counting devices with automatic magnetic code protection
control. Therefore the creation of such devices as well as the
development of infomrtion processing methods targeted to serve them represent a
new and actual problem.
To achieve the goal of the project it is planned to:
-
Continue research on the methods of data processing mentioned above to specify
the parameters of sygnal processing (wavelet types, filter characteristics) and
introduce the acquired results into development of data processing algorithms.
-
Acquire results of computer aided sygnal processing
-
Chose the best suited methods as a result of comparative analysis of the
results
-
Develop programming code implementing chosen data processing methods
-
Use the results of research to develop and modernize computer controlled
currency counters and validators
List of information sources
-
http://bankir.ru/analytics/antilegal/
,
Методы и оборудование для определения подлинности денежных знаков и ценных
бумаг
-
http://www.bre.ru/security/payment/
,
Аппаратурные средства проверки подлинности документов на основе оптического
метода неразрушающего контроля
-
http://money.dmd.ru/
author:Шапошников Ю.И. , book title: Деньги.Информация.
-
http://www.bankob.ru/catalog/counters/det/delarue/
Счетчики банкнот фирмы De La Rue (Англия)
-
http://www.bankob.ru/catalog/counters/det/pro/
Счетчики банкнот фирмы PRO (Япония)
-
http://www.bankob.ru/catalog/counters/det/scancoin/
Счетчики банкнот фирмы Scan Coin (Швейцария)
-
http://www.bankob.ru/catalog/counters/det/speed/
Счетчики банкнот фирмы SPEED (Япония)
-
http://www.spectr.nikolaev.ua/
Сайт компании-производителя средств пересчета и детекции валют НПО "Спектр", г.
Николаев, Украина
-
http://epos.kiev.ua/pubs/
С.Коженевский, С.Левый, В. Вишневский, С. Прокопенко
article: Методы визуализации магнитных полей носителей информации
-
http://www.lad.org.ua/index.html
Лаборатория методов и средств риминалистических исследований радиотехнического
факультета НТУУ КПИ.Сканер магнитной защиты документов "СЕЗАМ"
-
аuthor: Ефимов Е.Г.,книга: Магнитные головки, М., Энергия, 1967,350
с.370
-
журнал «CHIP News», №4 (24), май 2003
статья «Использование магнитных датчиков фирмы NVE в детекторах фальшивых
купюр».
-
author: Carl H. Smith
article: The color of money: using magnetic media detection to identify
currency.
-
author:А.Б. Сергиенко
book title: Цифровая обработка сигналов, Питер, 2002г., 606 с.
-
author: C.Valens
article: A really friendly guide to wavelets, 1999
-
author: Киселев А.
article: Приложения вейвлет-анализа, BaseGroup Labs
-
http:// www.basegroup.ru/labs/
article: Основы теории вейвлет-преобразования
-
Дремин И.М., Иванов О.В., Нечитайло В.А.,журнал «Успехи физических
наук», том 171, №5, май 2001, статья «Вейвлеты и их использование»
-
Астафьева Н.М., журнал «Успехи физических наук», том 166, №11, ноябрь 1996,
статья «Вейвлет-анализ: основы теории и примеры применения»
-
author: Naoki Saito
PhD thesis: Local feature extraction and it's applications using a library of
bases. ;186p.
Yale University
-
author:
Шитов А.Б.
PhD thesis: Разработка численных методов и программ, связанных с применением
вейвлет-анализа»
Ивановский Государственный университет, специальность «Математическое
моделирование, численные методы и комплексы программ»
Note:
presented autoreferat is not a final version of master's thesis autoreferat as
the current research is in course and is planned to be completed by 31.12.2006.
For the final version of master's thesis please e-mail the author.